So, you set up your VoIP phone system, but you’re experiencing dropped calls, no incoming calls, or your phone keeps ringing after you pick up.
The good news is that you will be able to instantly resolve your Voice over IP issues once you disable SIP ALG.
In this updated guide, we’ll cover why SIP ALG must be turned off, and we’ll include tips to optimize your network for VoIP phone service.
This guide is perfect for novices as well as advanced users. Let’s get started!

What Is SIP ALG?
SIP ALG is a feature found in most networked routers, operating as a function of its firewall. It consists of two different technologies, explained below:
- Session Initiation Protocol (SIP) – The underlying service that powers all Voice over Internet Protocol (VoIP) phones, apps, and devices. SIP manages registering devices, maintaining call presence, and overseeing the call audio. Read more about SIP in our deep dive here.
- Application Layer Gateway (ALG) – Routers segments your ISP and your internal network through a process known as Network Address Translation (NAT). An ALG acts as a proxy to rewrite the destination addresses in data packets for improved connectivity.
To break it down even more, let’s understand how SIP ALG works.
How SIP ALG Works
NAT traversal
In a typical network setup involving NAT, the internal IP addresses are translated into one or more external IP addresses. NAT generally complicates the traffic routing for protocols like SIP because SIP messages contain IP addresses in the payload. NAT changes the packet headers but not the payload, leading to mismatches between the IP addresses in the SIP headers and those in the payloads.
SIP ALG works by inspecting SIP packets and modifying SIP headers and SDP (Session Description Protocol) body to ensure the internal network’s private addresses are converted to public addresses where necessary, and vice versa. This helps in maintaining the consistency of the information as packets move between internal and external networks.
Modification of traffic
SIP ALG can alter the traffic passing through the NAT device. This includes changing IP addresses and ports in the SIP headers to match those used in the NAT. It might also involve adjusting the firewall’s dynamic pinholes to allow SIP traffic through.
Handling of SIP sessions
SIP ALG keeps track of active sessions and modifies the routing table to ensure that return packets follow the correct path back to the sender. It effectively manages session timeouts and ensures that the sessions are alive by possibly modifying the SIP keep-alive packets.
Resolution of SIP signaling and media paths
Since SIP signaling often involves multiple request and response messages, SIP ALG ensures these messages correctly reference the NATed IP addresses and ports. Furthermore, SIP ALG also ensures that the media paths (RTP/RTCP) are correctly established between the client and the server by rewriting the necessary packets.
The problem with SIP ALG is its packet rewriting. While it can be useful to mitigate multiple NATs, it doesn’t help the vast majority. Let’s take a more in-depth look at what’s happening with these data packets.
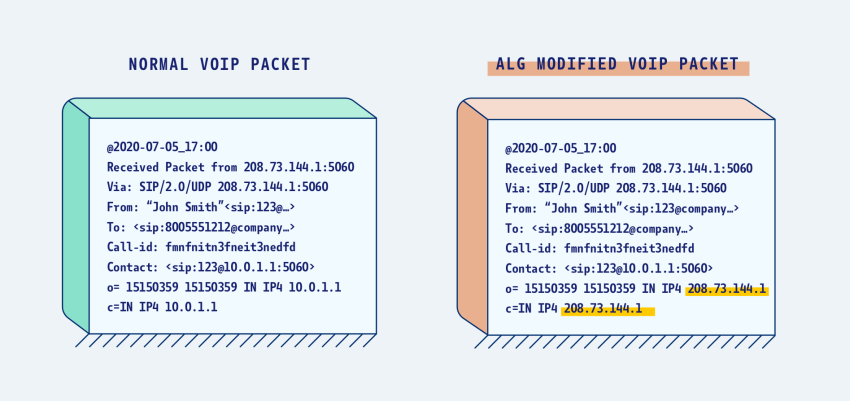
The diagram above shows that the Application Layer Gateway changes the destination public IPs in SIP packets. Certain commercial routers are smart enough to inspect the SIP messages themselves to leave private IP addresses alone.
Today’s office PBX systems, conference calls, and even audio/video conferencing rely on SIP. Signaling protocols like SDP, RTP, and RTSP all face the same issues because they are a subset of SIP packets.
If you need a little more context, watch our 2-minute video below explaining SIP ALG and why you may want to disable it.

Signs SIP ALG Affects VoIP Calls
There are a few categories of symptoms that SIP ALG could affect VoIP phones. These issues are not always apparent, especially since they often happen silently without users’ knowledge.
Call set-up issues
Symptom: Difficulty in making outgoing calls or receiving incoming calls.
Cause: SIP ALG may alter SIP INVITE requests and responses inconsistently. If the translated addresses in the SIP messages do not match or if essential information is lost during NAT handling, the call setup can fail.
One-way audio
Symptom: One party cannot hear the other, though the call is established successfully.
Cause: SIP ALG may incorrectly handle the RTP streams that carry the audio. If SIP ALG rewrites the IP addresses or ports in the SDP body but fails to open corresponding pinholes in the firewall for RTP traffic, it can result in one-way audio.
Dropped calls
Symptom: Calls are unexpectedly dropped after a certain duration.
Cause: This often occurs due to improper handling of the SIP keep-alive messages or incorrect management of NAT bindings and session timeouts. SIP ALG might not refresh the NAT bindings timely, leading to the expiration of NAT sessions.
Inconsistent call quality
Symptom: Variability in call quality, such as sudden drops in quality or periods of jitter and latency.
Cause: SIP ALG’s processing overhead for inspecting and modifying SIP packets can introduce delays or variability in packet transmission. This affects the RTP stream, leading to reduced call quality.
What’s happening is that some VoIP traffic is lost between the phone and the VoIP service provider. This interruption is happening because of router firewalls. This traffic is essential to maintaining the phone’s availability and selecting the proper audio codecs.
Many routers default SIP ALG to on within their device’s firmware. Thanks to easy and simple web interfaces, simply check or uncheck a box. Pictured below is an example:
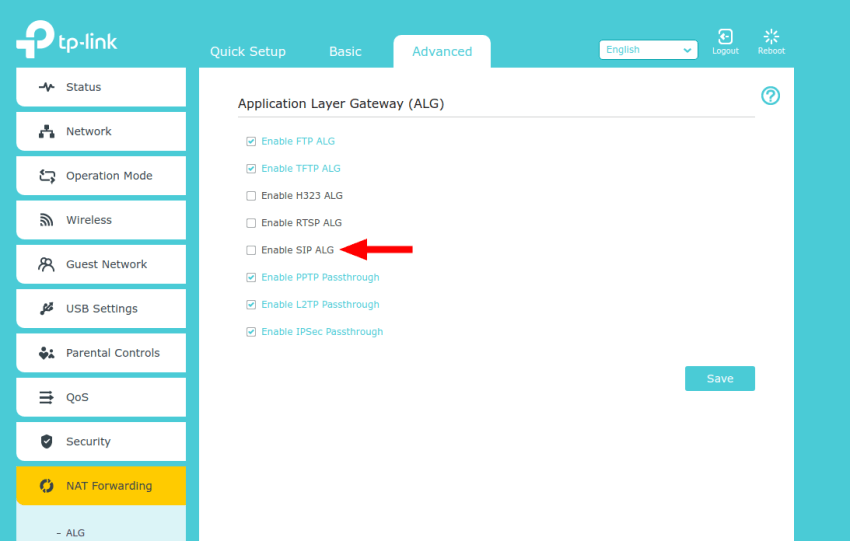
How Do I Turn Off SIP ALG?
To disable SIP ALG, you will need to log into your router. Your router can also function as a modem for some broadband gateways. Popular router brands include Cisco, Linksys, Netgear, D-Link, Asus, and TP-Link.
We’ve compiled a list of the top routers and included links to disable the Application Layer Gateway, which can interfere with VoIP calls.
In most cases, you will need to sign in to your router with the admin password. Look under its security settings, uncheck SIP ALG, save and reboot your router. More advanced corporate firewalls may require further adjustment, such as port forwarding.
| Router Manufacturer | Steps to Disable SIP ALG |
|---|---|
| Actiontec | 1. Select Advanced, click Yes to accept the warning, then click ALG’s. 2. Ensure SIP ALG is disabled by removing the check. 3. Click Apply. 4. Select Advanced, click Yes to accept the warning, then click Remote Administration. 5. Click the checkbox to Allow Incoming WAN ICMP Echo Requests (for traceroute and ping), then click Apply. 6. For more info, check out this support article. |
| Adtran | 1. Under Firewall, go to Firewall / ACLs 2. Click on ALG Settings. 3. Uncheck the box labeled SIP ALG 4. Click Apply. If you are using the terminal, issue the following command: no ip firewall alg sip |
| Arris | Most Arris broadband gateways: 1. Navigate to the gateway’s IP (192.168.0.1). 2. Username: admin Password: motorola 3. Navigate to Advanced, then Options. 4. Uncheck the SIP box. 5. Click Apply. Arris BGW210 1. Navigate to 192.168.1.254. 2. Authenticate without a username, and use the password located on the unit’s sticker. 3. Under the Firewall section, click on Advanced Firewall. 4. Change the Set SIP ALG setting to off. 5. Turn off the Authentication Header Forwarding. 6. Turn off ESP Header Forwarding 7. Click Save. |
| Asus | 1. Under the Advanced Settings section, click WAN. 2. Click the NAT Passthrough tab. 3. Change the SIP Passthrough setting to “Disable.” 4. Click Apply. |
| AT&T |
U-Verse Pace 5268AC Gateway |
| Cisco | Cisco General and Enterprise-Class routers: no ip nat service sip tcp port 5060 no ip nat service sip udp port 5060 Cisco PIX routers: no fixup protocol sip 5060 no fixup protocol sip udp 5060 Cisco ASA routers: Locate ‘Class inspection_default’ under ‘Policy-map global_policy’. Execute this command: no inspect sip |
| D-Link | 1. Click on Advanced Settings. 2. Locate the Application Level Gateway (ALG) Configuration. 3. Uncheck the SIP option. 4. Click Save. DIR-655: 1. Click Advanced, located along the top. 2. Click Firewall Settings on the left side of the screen. 3. Uncheck Enable SPI 4. Set both UDP and TCP Endpoint Filtering to Endpoint Independent. 5. Uncheck SIP from Application Level Gateway Configuration. 6. Click Save. |
| Fortinet | Use the following commands from the CLI interface: config system session-helper show system session-helper Find the SIP session instance, typically indicated by #12 Delete #12 or the appropriate number Confirm its deletion by executing this command: show system session-helper. For more guidance, follow this article. |
| Linksys | Linksys Smart Wi-Fi (E-series): 1. On the left side of the screen, click on Connectivity. 2. Click the Administration tab. 3. Under Application Layer Gateway, verify SIP is unchecked. 4. Click Apply or Save. Older Linksys models: 1. Go to the ‘Advanced’ section on the Admin page 2. Disable the SIP ALG feature. Linksys BEFSR41 routers: 1. Click on Applications and Gaming on the Admin page. 2. Click on Port Triggering. 3. Type in ‘TCP’ as the application. 4. Type in ‘5060’ into the Start Port and End Port for the ‘Triggering Range’ and ‘Forwarded Range’ fields. 5. Check ‘Enable’. 6. Click on Save and Reboot. |
| Mikrotik | For Mikrotik routers, SIP ALG is known as SIP Helper. 1. Use the company’s winbox software. 2. Navigate to IP, then Firewall. 3. Click on the Service Ports tab and disable it through the GUI. 4. You may also run this command from the terminal: /ip firewall service-port disable sip |
| Netgear | For Netgear routers with the Genie interface: 1. Select the Advanced tab at the top. 2. Expand the Setup menu on the left side of the screen. 3. Click WAN Setup. 4. Check the box labeled Disable SIP ALG. Other Netgear routers: 1. Under the Security/Firewall, click on Advanced Settings. 2. Disable SIP ALG. 3. Locate Session Limit under Security/Firewall. 4. Increase the UDP timeout to 300 sec. |
| SonicWall | 1. Under System Setup on the left side of the screen, click on VoIP. 2. Check ‘Enable Consistent NAT’ 3. Uncheck ‘Enable SIP Transformations’. 4. Click Accept. 5. To increase UDP timeouts, navigate to the Firewall Settings, then Flood Protection. 6. Click on the UDP tab and modify the default UDP connection timeout to 300 seconds. 7. Click the Accept button to save the changes. For more information, consult this support article. |
| TP-Link | Newer TP-Link routers (Archer series): 1. Click on the Advanced Tab. 2. Expand the NAT Forwarding menu on the left side of the screen. 3. Uncheck SIP ALG, RTSP ALG, and H323 ALG checkboxes. 4. Click Save. Older TP-Link routers: 1. Use the Telnet client from the Command Prompt. 2. Apply the following command: ip nat service sip sw off |
| UBEE | 1. Go to Advanced, then Options. 2. Uncheck the SIP and the RTSP checkboxes. 3. Click Apply. |
| Ubiquiti | UniFi Security Gateway 1. Sign in to your UniFi security gateway. 2. Click on Routing & Firewall along the left side. 3. Click the Firewall tab at the top and click Settings from the sub-menu. – Toggle H.323 and SIP to off. – Click the Apply Changes button. EdgeRouters (ER-x) 1. Access the router’s administrative interface, typically at 192.168.1.1. 2. Use the Config Tree or a command-line interface to disable SIP ALG. Config Tree: 1. Select config tree in the top right-hand corner. 2. Expand system, conntrack, modules, and sip. 3. Click the plus sign next to disable. 4. Click the Preview option. 5. Click Apply. Command Line Interface: 1. From the administrative interface, choose CLI located at the top right corner of the screen. 2. From here, we can also increase UDP timeouts as well. 3. Enter these commands into the terminal: configure – set system conntrack modules sip disable – set system conntrack timeout udp stream 300 – set system conntrack timeout udp other 300 – commit – save – exit |
| Verizon FiOS | G1100 This broadband gateway does not support disabling SIP ALG. We recommend configuring your gateway to function only as a modem, not a router. You will need to use another router that supports disabling SIP ALG. |
| ZyXEL | ZyXEL ZyWALL/USG60: 1. Click on Configuration and expand the Network settings. 2. Click ALG along the left side. 3. Uncheck all the checkboxes on the right side: – Uncheck Enable SIP ALG. – Uncheck Enable SIP Transformations. 4. Click Apply. ZyXEL C1000Z/C1100Z (CenturyLink): 1. Click on Advanced Setup.Click on SIP ALG along the left side. 2. Toggle the SIP ALG setting to Disable. 3. Click Apply. ZyXEL P600: 1. Telnet to the router (192.168.1.1) and enter the password. The default password is 1234. 2. Type “24” and press enter. 3. Then “8” and press enter. 4. Provide this command: ip nat service sip active 0 5. When done, press Enter. |
Why Disable SIP ALG?
Conventional wisdom would suggest that an Application-Level Gateway is supposed to be enabled. After all, many consumer and commercial router settings even default SIP ALG to on.
As a feature in most broadband routers, SIP ALG was introduced with good intentions in response to the limitations of Network Address Translation. Unfortunately, it interferes with the built-in functionality of IP and signaling protocols. It’s no longer necessary with today’s VoIP applications.
Since ALGs exist at the Application Layer of the OSI Model, it doesn’t consider the datagrams within transport protocols like UDP or TCP. VoIP signaling protocols solve these common issues by including the public and private IP addresses in every packet.
Some routers try to improve security by terminating open connections in the firewall. Dubbed a “firewall pinhole,” it means that traffic can work momentarily, but when a SIP proxy drops packets, it can affect VoIP calls after you establish them.
You should disable SIP ALG because it:
- Interrupts SIP traffic like calls and conferencing apps.
- Affects the perceived reliability of desk phones and VoIP apps.
- Isn’t needed when using cloud-based VoIP providers.
For almost all VoIP users with a virtual phone service, the best practice is to turn off SIP ALG entirely.
The only reason why you would enable SIP ALG is if your router manufacturer or VoIP provider has instructed you. Given the prominence of VoIP and Application Layer Gateways, they will provide proper settings to work with your VoIP provider.
Best Practices for Reliable VoIP Performance
Voice over Internet Protocol (VoIP) demands a few basics for optimal phone calls. In short, that’s bandwidth, latency, and stability. Follow these tips to improve inbound and outbound call quality and connectivity for your team.
1) Choose a high-bandwidth ISP with the proper hardware
High-bandwidth connections reduce the likelihood of packet loss and delays, which are common issues in VoIP systems and can lead to garbled or dropped calls.
Additionally, ISPs that specifically cater to businesses often provide SLAs that guarantee minimum bandwidth and uptime, essential for businesses relying on constant and consistent communication capabilities.
It’s also important to consider the geographical coverage of the ISP, ensuring that it provides strong and consistent service in the areas where your business operates, as this directly impacts call quality and reliability.
Alongside choosing the right ISP, investing in the proper hardware is another vital step. Routers and modems designed for VoIP usage can prioritize VoIP traffic through QoS settings, helping to ensure that voice traffic is prioritized over other types of network traffic, like file downloads or video streaming. This prioritization is important as it prevents delays and packet loss during peak usage times.
Furthermore, advanced hardware options such as VoIP gateways and session border controllers (SBCs) can provide additional features like traffic shaping, security protocols, and failover capabilities, enhancing the VoIP communication infrastructure.
2) Use wired Ethernet connections whenever possible
Ethernet provides a more stable and faster connection compared to wireless setups, which can be prone to interference and fluctuations in signal strength. Issues such as data packet loss, jitter, and latency are significantly reduced when using a wired connection. These factors are critical in VoIP communications, where even minor delays or loss of data can result in poor audio quality or disrupted service.
Furthermore, Ethernet connections ensure that the bandwidth capacity allocated to VoIP devices is consistently maintained without being affected by other devices on the network, which is a common challenge in wireless environments.
The reliability of wired connections also extends to security aspects. Wired networks are inherently more secure than wireless networks, as they require physical access to connect to the system. This reduces the risk of eavesdropping or hacking, which are more prevalent in wireless setups due to the ease of remote access.
For businesses, the security of communications is key, particularly when handling sensitive or confidential information over VoIP calls. Additionally, wired setups are generally easier to manage and troubleshoot compared to wireless networks, leading to reduced downtime and maintenance costs.
3) Lengthen your UDP timeouts
UDP is commonly used for VoIP communications because it offers low latency transmission without requiring a handshake, unlike TCP.
However, UDP’s connectionless nature means that sessions can be terminated prematurely by network equipment like firewalls or routers if they are configured with short timeout settings.
By increasing the UDP timeout settings, you extend the duration that the network equipment considers the connection valid, reducing the likelihood of dropped calls or interrupted service due to premature session closures.
This is particularly important in scenarios where call setups might take longer or in complex network environments where devices frequently go through different states of connectivity.
Adjusting the UDP timeout settings can also improve the resilience of the VoIP system to network inconsistencies, such as varying latency or packet delays, by providing a more stable connection state over longer periods.
It is essential to balance the timeout settings to avoid excessive consumption of network resources or potential security risks from overly long timeouts. The optimal settings typically depend on the specific network infrastructure and usage patterns, and may require periodic adjustments as network conditions evolve.
💡 Pro Tip → Set your UDP timeouts to 150 seconds. If you find that your network routes get congested often, consider switching your VoIP setup over to Transmission Control Protocol (TCP). This tweak will increase your VoIP reliability. Consult with your VoIP service provider for further guidance.
4) Set up Virtual LAN (VLAN) tagging for SIP devices
VLANs create separate network segments within a larger network, dedicating specific pathways for VoIP traffic. This segregation helps in managing network traffic more efficiently, as it isolates SIP devices from the bulk of the network’s data traffic, such as large file transfers or streaming video, which can consume significant bandwidth and interfere with voice data packets.
By setting up a VLAN for SIP devices, network administrators can ensure that voice traffic is given priority, which is crucial for maintaining the QoS. Moreover, VLANs can scale as business needs grow, allowing for the addition of more SIP devices without compromising the performance of existing network services.
Furthermore, VLAN tagging enhances network security by segmenting traffic into distinct, manageable sections. Each VLAN can be configured with its own security protocols, effectively containing potential breaches to a single segment of the network and thereby protecting the rest of the network infrastructure.
This is especially valuable for SIP devices, which, if compromised, could expose the entire network to vulnerabilities. VLANs also simplify the management of network policies and enable better troubleshooting capabilities by allowing network issues to be isolated quickly.
💡 Pro Tip → After approximately 15 users, we recommend implementing network prioritization using Quality of Service (QoS). VLAN tagging lets you prioritize VoIP data above non-essential traffic. Doing so will minimize packet loss and enhance your overall VoIP security.
5) Keep up on firmware updates
Take an active approach in checking for your router manufacturer’s firmware patches. These may sometimes revert settings, but they will patch security and performance issues. You may need to consult with the vendor to download updates from its FTP or push software images via the Command Line Interface (CLI) for commercial routers.
Selecting the Right VoIP Phone Service
Disabling SIP ALG can be the solution to many problems when making calls with VoIP. Many technicians often overlook this simple fix. It’s undoubtedly worth adjusting to enhance the overall reliability and performance of your virtual phone service.
You’re likely reading this article because your phone system isn’t working right. It happens to the best of us. Instead of trying to fix this on your own, you could talk with one of our VoIP experts.
Nextiva has been providing companies a better choice for commercial phone service for over 15 years. Unlike telephone and cable companies, We cater only to businesses. Arguably, we deliver the best live support, which is why we call it Amazing Service®.
The best business phone service for less.
Simplify team communication with the top-rated phone system for small businesses. Save hundreds over landlines.
















 VoIP
VoIP