VoIP phone systems differ from traditional setups because you don’t need copper wiring that spans across your entire office. Connections are made virtually using an internet connection.
But that often causes a big security vulnerability: everything is hosted in the cloud.
In this guide, we’ll go over what VoIP hacking is, the most common types of hacks to look out for, how to prevent a breach of your VoIP network, and how to improve your VoIP security.
What Is VoIP Hacking?
VoIP phone systems have different network security risks than other traditional phone systems due to their setup.
VoIP hacking is a type of security attack in which hackers infiltrate your business phone system. They can listen in on calls, rack up expensive bills, and steal sensitive information – both about your business and your customers.
VoIP hacks most often happen when one of your employees accidentally gives information to a scammer. This type of scam is called “social engineering” and accounts for 97% of all malware attacks.
How VoIP hacking works
Hacking a Voice Over Internet Protocol phone system isn’t as far-fetched as you might think. The Internet of Things (IoT) world we now live in means that basically everything is done online – including most phone systems – which makes security more challenging.
Hackers target people working in customer service and in the Network Operations Center (NOC), by calling and acting as someone else – such as a vendor or customer. Make no mistake, these cybercriminals are talented actors. Staff can unknowingly give unauthorized access to the authentic-sounding hacker, who then takes control of your VoIP phone system.
And gaining access to your business’ phone system can launch other attacks. For example, a VoIP hacker could access the information to charge your credit card, impersonate your business, and acquire private customer data.
This is why it’s crucial to stay current on the ways business phone systems are compromised and review the steps you and your provider can take to secure communications. (More on this below.)

Six Types of VoIP Hacking
VoIP hacking exploits vulnerabilities in Voice over IP (internet protocol) systems to steal data, make unauthorized calls, or disrupt services. Here are the six most common types of VoIP hacking you need to be aware of.
1. Unauthorized use
This type of attack is when hackers use your business’ phone system to make unauthorized phone calls or to use robocalling and auto-dialing software.
People who answer the phone with your business’ caller ID will hear a pre-recorded message asking them to do something — such as enter their credit card number to “confirm their account.” It isn’t your business making the call, though. The hacker now has access to all of that customer’s private information.
2. Toll fraud (phreaking)
Toll fraud occurs when hackers gain unauthorized access to a VoIP system and make expensive international or premium-rate calls, charging them to your business. Toll charges for these long-distance phone numbers can be extremely high and will be billed to your account.
Hackers often gain access to a VoIP system through weak passwords, security vulnerabilities, or VoIP phishing (vishing) attacks. Once inside, they can reconfigure call settings, route calls through your system, or sell access to fraudulent callers.
3. VoIP phishing (vishing)
VoIP phishing, or vishing, is a social engineering scam where attackers impersonate a trusted entity over the phone to trick victims into revealing sensitive information, such as login credentials, financial details, or security codes. Vishing often works in coordination with other VoIP threats, such as toll fraud and caller ID spoofing.
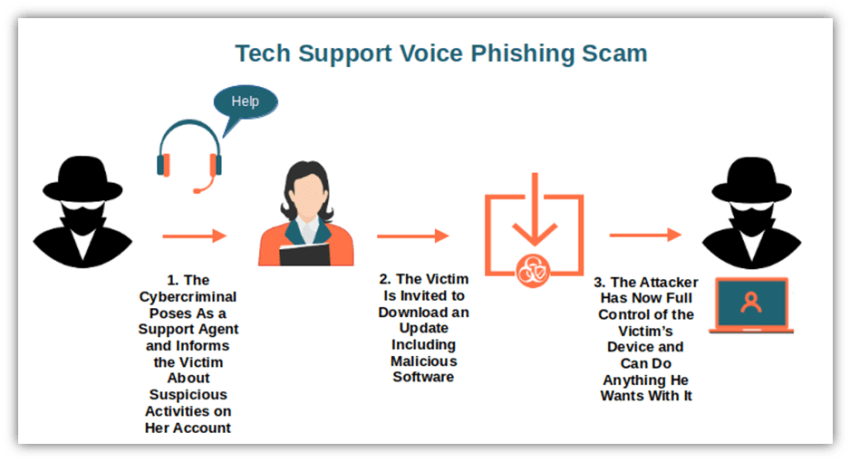
For example, hackers may leave a voicemail for your finance team, pretending to be your VoIP provider or bank. The message asks them to verify banking information or provide security codes. If an employee unknowingly calls back and shares the requested information — such as a VoIP system password or an IP address — the hacker can use these credentials to break into your VoIP system and commit toll fraud.
4. Caller ID spoofing
Caller ID spoofing is a technique where hackers manipulate the displayed caller ID to make it look like a legitimate number, such as your VoIP provider, bank, or a company executive. This tactic is often combined with vishing scams to make fraudulent calls seem more credible.
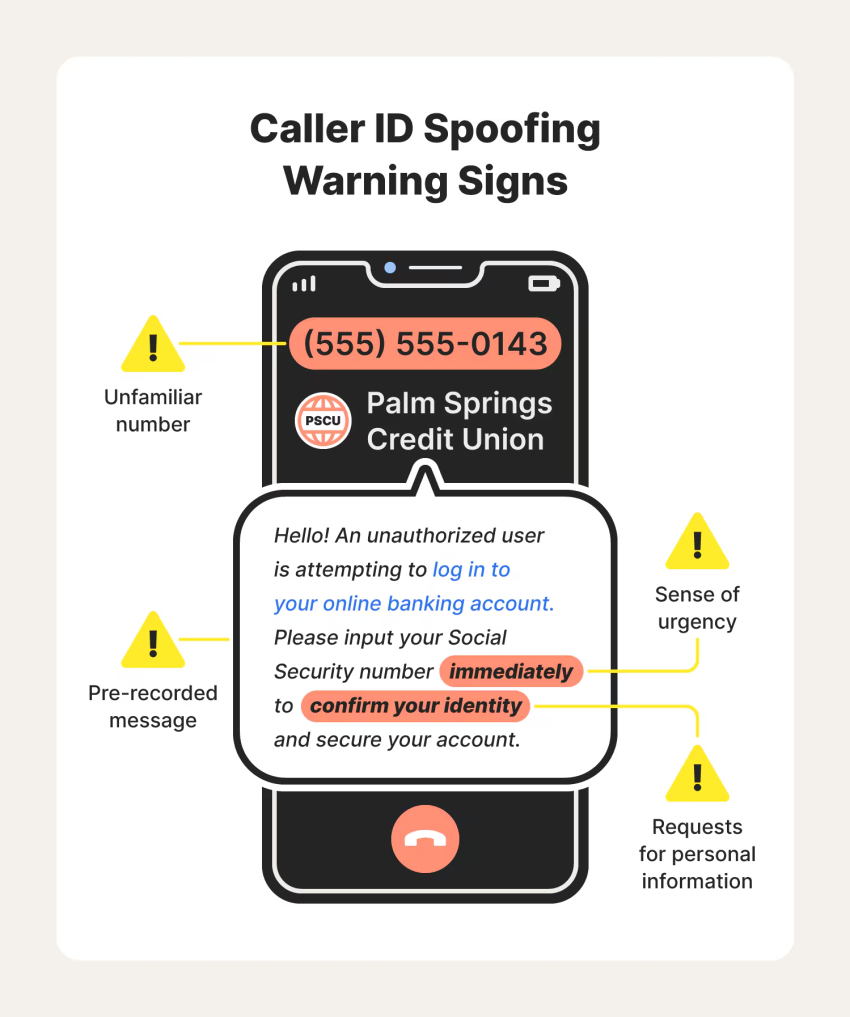
Employees often trust calls that appear to come from familiar numbers, making them more likely to disclose sensitive information. For example, an employee might receive a fake call from “IT Support” asking them to reset their VoIP system password. If they comply, the hacker can gain access to your system, reroute calls, or launch further attacks.
5. Eavesdropping
If you take payments over the phone, you’ll need to prevent eavesdropping. This is when hackers listen in on your real-time business phone calls or recordings like voicemails and then collect information on your company and your customers to either sell or use illegally.
Eavesdropping is only possible when the connection is unencrypted or the local network itself is breached. Insecure Wi-Fi networks — those without Transport Layer Security (TLS) and Real-time Transport Protocol (SRTP) — make it easy for attackers to monitor the network.
6. Social engineering
While all vishing attacks are social engineering, not all social engineering attacks involve vishing.
Social engineering is a common type of VoIP hack because it preys on people, not technology. Hackers try to build relationships with their victims so they think it’s a genuine call, but it’s not. The call is a hacker impersonating someone else to trick you into handing over sensitive information.
This can include false account requests, like verifying your account, and then harassing or threatening victims based on the data they’ve acquired. These emotionally charged situations compel staff into doing something under pressure, and that going against proper procedure in this case is the right thing to do.
Signs You’re the Victim of VoIP Hacking
Here are five signs that your business’ VoIP system may have been hacked:
- Unusual Call Activity – Unexpected international or long-distance calls appearing on call logs, especially to high-cost regions, may indicate toll fraud.
- Poor Call Quality or Dropped Calls – A sudden increase in call delays, echoes, or dropped calls could mean a hacker is overloading your system with a Denial-of-Service (DoS) attack.
- Unauthorized Account Access – If VoIP users notice password resets, strange logins, or settings changes they didn’t make, a hacker may have gained access.
- Increased VoIP Bills – Unexpectedly high charges on your VoIP account can signal that an attacker is making unauthorized calls at your expense.
- Suspicious Voicemails or Phishing Attempts – Receiving strange voicemails, robocalls, or messages asking for sensitive information may indicate a security breach or an attempt at social engineering.
11 Tactics to Protect Your VoIP System from Being Hacked
Each of the VoIP hacks listed above are costly for businesses — and not just economically. It’s also time-consuming to fix and damaging to your business’ reputation.
But it’s not all bad news. Most VoIP vulnerabilities can be eliminated with better awareness, regular education, and proactive steps your internal team can take to strengthen your defenses.
Here are 11 things to do to help prevent your business’ VoIP system from coming under attack.
1. Choose the right VoIP provider
A secure phone system starts with the VoIP provider you’ve chosen.
A weak provider makes it easier for hackers to infiltrate your phone network and gain access to private information. Always check their security policy before you take out a contract with any VoIP service provider and make sure they:
- Are transparent about their network’s security
- Have a plan of action if a hack does occur
- Have accreditations that prove their security is up to date
- Share a responsible security disclose program
They should be able to give you this information on request. If they don’t, move on to a different VoIP provider.
2. Control administrator access
Administrative access to your VoIP infrastructure means the user can control everything related to your business phone system, including manage billing, join conference calls, set up new lines, and lead to more costly intrusions.
Giving everyone access to your VoIP phone system increases the likelihood of a social engineering attack, so don’t give administrative control to people who don’t need it. Also, conduct user access reviews on a regular basis:
The more employees with admin control, the higher the risk that someone will give a hacker administrative access to your network.
3. Use a VPN for remote access
Remote staff communicate with their coworkers and customers via phone, which makes them vulnerable to VoIP hacking. However, a Virtual Private Network (VPN) encrypts those phone calls:

Your remote team installs a VPN on their work devices — including their smartphone or softphone. This creates a secure connection between that device and your phone system, just as you’d have in the office. That makes it almost impossible for hackers to eavesdrop on the calls your remote workforce are making.
4. Enable endpoint filtering
VPN providers such as Sophos and Cisco use endpoint filtering to block the network from accessing malicious sites that could download malware or handing over information hackers can use against you, such as a public IP address. This strengthens overall network connectivity and device integrity.
It’s also a good idea to have a Wi-Fi Security VPN to secure your connection from cyber criminals. There are a number of solutions that provide this added layer of protection. Aura — a Wi-Fi security VPN company — tracks about 350K malware programs every day.

5. Regularly test your network
It’s not unusual for small businesses to set up their VoIP system and never look at it again – which leaves you at risk for a VoIP hack. Regularly checking your network allows you to spot any vulnerabilities in your VoIP security, such as:
- Staff who left the company two years ago still have accounts
- Your admin passwords haven’t been changed in two years
- The connection gateway doesn’t have Transport Layer Security (TLS) or Real-time Transport Protocol (SRTP), which means VoIP calls aren’t encrypted
Your IT department should also conduct an annual security check, called a “penetration test,” which simulates a security threat and determines whether the network is secure. Any potential weaknesses should be reviewed and fixed as soon as possible.
6. Monitor call and access logs
A call log is the history of incoming and outgoing calls your business has made. It’s not just useful for sales purposes, though. Access to these call logs mean you’re able to see:
- The date and time of each call
- How many calls you’re making to a specific number
- The location of your calls, both the business’ side and your customer locations.
You can easily see whether your VoIP phone system has been hacked with these logs. Regularly monitoring your call logs means you’ll get to know what “normal” looks like. Any anomalies that might signal a hack can be spotted — even before your call limits stop them.
Similarly, an access log shows who has signed into your VoIP phone system. If you spot an unusual IP address, or see that your administrator signed in at two in the morning (when they were asleep), you’ll spot an intruder.
7. Build awareness around strong passwords
When you’re setting up your VoIP solution, your provider will give you a default password to get started. But it’s crucial to change that password as soon as possible.
For a truly secure VoIP phone system, teach your employees about strong passwords. Avoid the most common passwords or using the same one for different accounts:
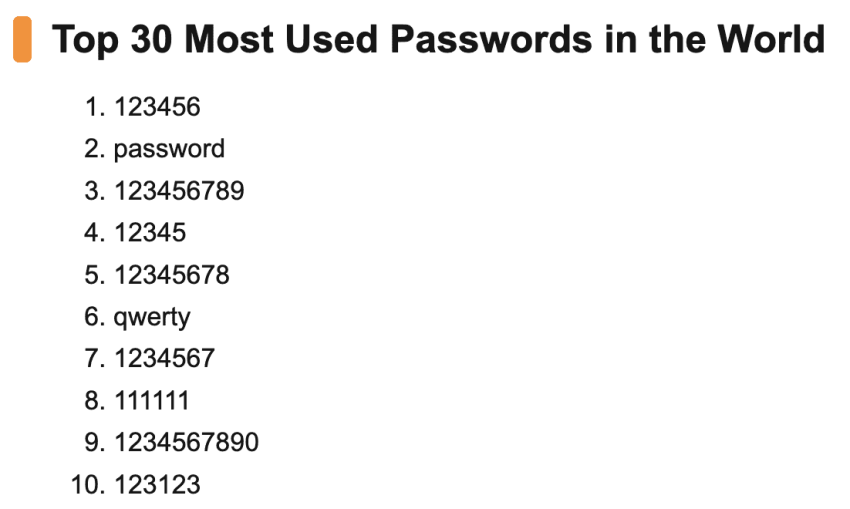
Repeat password usage, known as credential stuffing, means that if a hacker can figure out a customer service agent’s Facebook password, they’ll try the same combination on your VoIP phone system.
Security experts at Black Hills recommend creating passwords that are lengthy and include exclamation points, capital letters, and special characters. It’s harder to crack a 20-character password than one with eight letters. Then, rather than write them down on a sticky note or save them in an email – both of which are relatively easy for hackers to find – have your staff use a password manager:
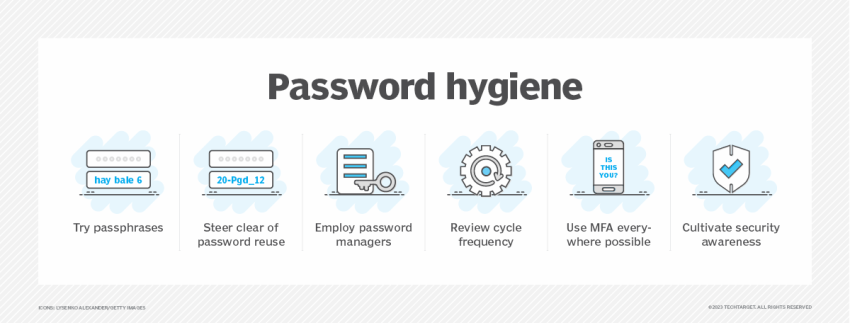
8. Use two-factor authentication (2FA)
Having said the above, it’s not impossible for smart, experienced hackers to crack a lengthy, complex password — hence why you should also have two-factor authentication for your VoIP phone system. Two-factor authentication (2FA) adds another layer of security on top of your password and requires users to authenticate a sign-in by:
- Having a code texted to their personal smartphone
- Scanning a QR code with an authenticator app
- Using their fingerprint ID
With one of these additional authentication features, hackers won’t be able to gain access to your VoIP solution, even if they have your password.
9. Train your team on cybersecurity
Just one security hole in your phone system can leave you exposed to a VoIP hack. The same concept applies to your staff, too: One uneducated employee might make a mistake that causes an expensive data breach in your business phone system.
Whenever you’re onboarding your staff, provide a mini-education on cybersecurity. Explain the importance of a strong password, install a VPN on their device, and educate them on the different types of VoIP hacks, especially social engineering.
But remember: Security isn’t a one-and-done job. Make it a priority to schedule regular cybersecurity training for your team members so they don’t get lazy.
10. Implement a mobile device management policy
Most employees use three or more devices while at work, such as their personal device or another laptop:

Each of those devices need to be up-to-par security-wise. Make sure your staff’s personal devices aren’t creating a vulnerability in your phone system — especially if they’re using those devices to make business VoIP calls — by having a mobile device management policy with details like:
- All personal devices must be connected to the Wi-Fi network for encrypted voice conversations
- The software on the mobile device must be up-to-date if it’s being used for business purposes
- All smartphones must have fingerprint ID to unlock the device
- Staff must report any stolen or misplaced devices immediately
11. Develop a response plan for breaches
Hackers are getting smarter, and they’ve got access to a growing number of tools to gain access to your business phone system. Sometimes, your in-house security tactics aren’t strong enough to deter them.
So you should always have a data breach response plan in place, regardless of how strong your security measures are. This document outlines what you’ll do in the event (or inevitability) of an attack.
How to Choose a Secure VoIP Provider
You can help make your VoIP phone system more secure, but sometimes, data breaches are a result of your VoIP provider’s mistakes.
Here are seven ways to confirm whether your provider is doing their part.
1. Check for accreditations (like HIPAA compliance)
Accreditations are certificates that prove your chosen provider meets industry-standard security standards. If your business operates in specific industries, you’ll need your VoIP provider to have those specific accreditations, too.
Healthcare for example, gets the most cyber-attacks because hackers can gain access to tons of sensitive, personal data. The Health Insurance Portability and Accountability Act (HIPAA) aims to help businesses secure health-related data, so your VoIP provider must HIPAA compliant if you’re in this sector.
2. Look for intrusion prevention systems
An intrusion prevention system prevents hackers from accessing your VoIP phone system and usually comes in two parts:
- VoIP traffic tracking: Your VoIP phone provider should be able to track traffic on your phone network. Too many incoming calls could be a DDoS attack. Monitoring this traffic can block the calls before your network gets overwhelmed and shuts down.
- Alerts for suspicious activity: The warning signs of a VoIP hack can include an influx of calls, more international calls, or logins from other devices. Look for a VoIP provider that alerts you when these things happen so you can remove the risk.
3. Make sure there’s call encryption
Hackers can gain access to your VoIP system through insecure internet connections. Once they’ve got into your Wi-Fi network, they can eavesdrop on all network traffic, including calls coming in and out of your office. Transport Layer Security (TLS) hides the data being transferred from the data center to your VoIP devices. It also authenticates that the person behind the call is who you expect them to be, making it more obvious when a caller ID is being spoofed.
Encrypted voice conversations add an extra layer of security to your internet connection. With TLS from your VoIP provider, it’s almost impossible for a hacker to pick-up on call data you’re passing through your phone network.
4. Update firmware on VoIP devices
Almost every piece of business software releases regular updates. These refreshes to the actual firmware can release new features, repair bugs — and more importantly, fix security holes. It’s crucial to make sure the firmware your VoIP provider supplies is always up to date. You can check whether the provider will install these updates for you.
But if not, you should be able to sign into your online account and do it manually. Remember to do this on all your VoIP devices, too. One device running with weak, old firmware might be the hole hackers need to control your phone system.
5. Set VoIP call limit options
Earlier, we mentioned that one of the most common VoIP hacks is caller ID spoofing. It happens when a hacker gains access to your VoIP network and uses your account to make expensive long distance calls. However, your VoIP provider can help protect against attacks.
Check for features that limit calls by:
- Time of day
- Device
- User
That way, a large influx of calls gets flagged immediately. The hackers using your information to make long-distance calls are spotted (and blocked) before they rack-up any huge bills.
Checklist to Protect Your VoIP Phone
Here’s a quick checklist of the best tactics to prevent VoIP hacking, for easy reference.
- Choose the Right VoIP Provider
- Control Administrator Access
- Use a VPN for Remote Access
- Enable Endpoint Filtering
- Regularly Test Your Network
- Monitor Call and Access Logs
- Build Awareness Around Strong Passwords
- Use Two-Factor Authentication
- Train Your Team on Cybersecurity
- Implement a Mobile Device Management Policy
- Develop a Response Plan for Breaches
Nextiva’s VoIP Security Helps Protect Your Phone System
VoIP is a secure phone system that’s more reliable and modern than a traditional phone system. But with everything stored in the cloud, you need extra security features to make sure your setup is secure.
There’s no better time than now to check whether your VoIP phone system is airtight. Just the smallest security hole can expose your data to hackers, who can use that information against you and your customers. But remember, the provider you’re choosing is just as important as the precautions you take.
Here at Nextiva, our cloud PBX system has the security features we’ve mentioned, and more. Plus, our network is backed by eight military-grade data centers. To say we’re committed to security is an understatement.
The best cloud PBX phone system.
Get cloud-based VoIP, SMS messaging, and video conferencing in one solution. Keep your business communications safe and secure with Nextiva.
VoIP Hacking FAQs
Yes, VoIP can be hacked if it is not properly secured. Cybercriminals can exploit vulnerabilities in any VoIP system to eavesdrop on calls, steal data, hijack accounts, or launch attacks like toll fraud and Denial-of-Service (DoS). To prevent VoIP hacking, businesses and individuals should use encryption, strong authentication, firewalls, and regular security updates.
Yes, VoIP phones can be hacked. In addition to software, hackers can attack VoIP hardware devices, such as IP phones, VoIP gateways, and PBX (Private Branch Exchange) systems, by exploiting security weaknesses in firmware, configurations, network access, and authentication methods.
Cybersecurity plays a critical role in preventing VoIP hacking in several ways:
🔹 Multi-factor authentication (MFA) and strong passwords helps block unauthorized access.
🔹 TLS and SRTP encryption protect VoIP traffic from eavesdropping.
🔹 Firewalls, Intrusion Detection Systems (IDS/IPS), and VoIP-aware security tools prevent attacks like SIP flooding and toll fraud.
🔹 Regular firmware updates patch vulnerabilities.
🔹 Employee training helps prevent phishing (vishing) scams.
















 VoIP
VoIP