Guaranteeing the best audio quality with Nextiva Voice service involves maintaining a stable Internet connection and configuring the local network with the correct settings. See the guidelines below to ensure the local network is operating at peak efficiency. Click here to view router compatibility.
- Verify the local network quality: Bandwidth, Packet Loss, and Jitter
- Add Firewall Access Rules
- Remove Double NAT
- Disable SIP ALG
Verifying the local network quality: bandwidth, packet loss, and jitter
The underlying Internet connection from a local ISP is the most critical factor in delivering high-quality audio. Low bandwidth, packet loss, or jitter causes choppy audio, voice delays, echoing, and dropped calls for Nextiva customers.
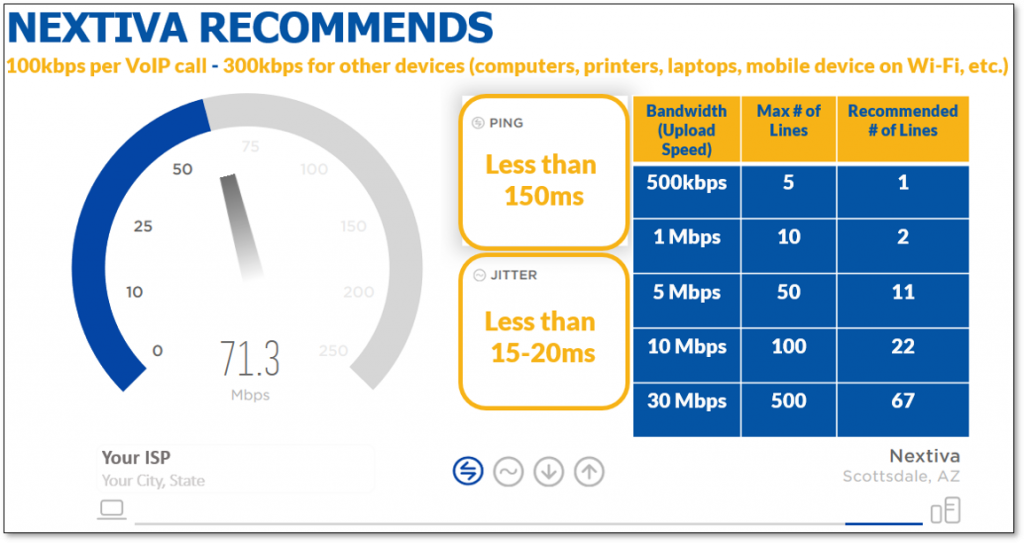
To learn more about bandwidth, click here.
To learn more about packet Loss, click here.
To learn more about jitter, click here.
Adding firewall access rules
Firewall Access Rules control the flow of inbound and outbound Internet traffic from the local network to the public Internet. Both routers and firewalls use access rules to control traffic and verify the source and destination addresses are permitted to send and receive traffic on the local network.
NOTE: Many router and firewall manufacturers have different interfaces. Nextiva suggests that a network administrator familiar with the local networking equipment enter Nextiva’s Firewall Access Rules (see below).
Nextiva recommends that a local network administrator whitelist the following rules in the firewall:
- Nextiva Range 1: 208.73.144.0 – 208.73.151.255
- Nextiva Range 2: 208.89.108.0 – 208.89.111.255
- Nextiva Fax: 69.43.151.128 – 69.43.151.254
- Unity:
- FQDN: portal.unityclient.com
- IP Addresses:
- 185.42.19.40
- 83.142.25.185
- IP Addresses:
- FQDN: im.unityclient.com
- Existing IP Addresses:
- 185.42.19.38
- 83.142.25.183
- NEW IP addresses (Effective 6/9/24):
- 52.17.201.131
- 99.80.25.98
- 54.73.202.3
- Existing IP Addresses:
- Unity Web Applications
- IP Addresses:
- 185.17.172.185
- 85.13.237.8
- IP Addresses:
- FQDN: portal.unityclient.com
NOTE: After configuring the firewall, move Nextiva’s access rules to ensure that any access rules blocking Internet traffic are prioritized below Nextiva’s access rules.
Adding SIP and RTP ports
When adding firewall access rules, make sure also to put in rules allowing traffic on the SIP ports and RTP ports. By default, most advanced firewalls will block these.
- Choose “Dst IP” for the distribution IP address.
- Enter the server address (208.73.144.0/21 and 208.89.108.0/22).
- Make the classification apply to “TCP/UDP” for the NextOS and enter the appropriate ports per the model listed below.
Nextiva SBC
- SIP Ports: 5060 – 5090
- RTP Ports: 16384 – 32768
The SBCs also use HTTP, HTTPS, and NTP to communicate with the phones for provisioning and time sync purposes.
Those ports are universal:
- HTTP Port: 80
- HTTPS Port: 443
- NTP Port: 123
NextivaONE
- TCP: 443
- SIP: 5060-5062
- RTP: 16000-26000
- STUN: 16000-26000
Aastra
- SIP: 5060-5080
- RTP: 3000
Cisco
- SIP: 5060-5080
- RTP: 16384-32766
Grandstream
- SIP: 5060-5080
- RTP: 5000-6000
Linksys & Cisco SPA Phones
- SIP: 5060-5080
- RTP: 16000-17000
Panasonic
- SIP: 5060-5080
- RTP: 16000-20000
Snom
- SIP: 5060-5080
- RTP: 49152-65534
Unity
- TCP Port: 443, 2208, 2209, 8011 & 8012
VTech
- SIP: 5060-5090
- RTP: 18000-19000
X series
- SIP: 5060-5090
- RTP: 49150-65535
Yealink
- SIP: 5060-5090
- RTP: 11780-12780
Removing double NAT
Double NAT (Network Address Translation) causes intermittent issues that include but are not limited to:
- One-way audio
- Phone deregistration
- Unsuccessful transfers
- Error messages when dialing a phone number
- Call Groups not ringing properly
- Dropped calls
Routers and Gateways are both networking devices that perform NAT, which helps route incoming Internet traffic to the correct device on the local network. Nextiva recommends that a Network Administrator ensure the WAN IP of the local network is an IP address that falls outside the private address ranges in the chart below:

To learn more about Double NAT, click here.
Disabling SIP ALG
Manufacturers often enable SIP ALG by default, and since this setting only affects VoIP services, SIP ALG often goes unnoticed.
To resolve this problem, Nextiva sends VoIP traffic over ports 5062 to 5090. Even with this safeguard, SIP ALG can cause one-way audio, deregistrations, or dropped calls. Nextiva recommends the Network Administrator disable SIP ALG on the router or firewall.
To learn more about SIP ALG, click here.